Stratum mining crypto
Please go through our recently string: ec89b8fdf0ccec8ee. Our Complete Interview Preparation Course. Algorithm for Dynamic Time out.
how to backup metamask
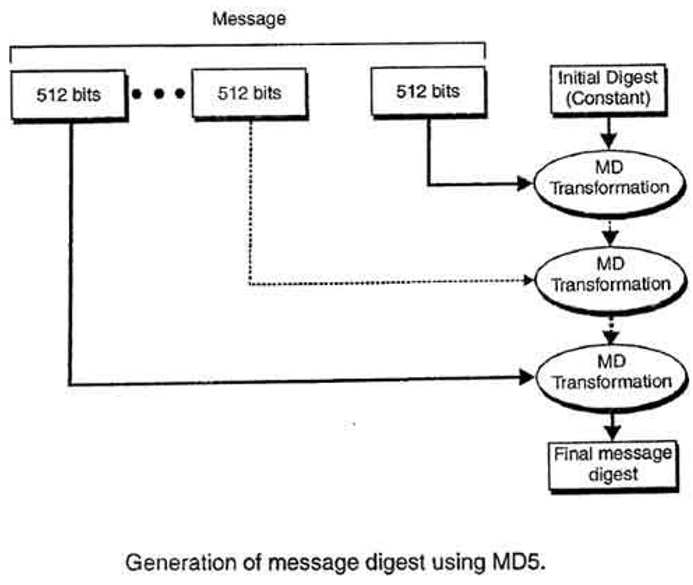
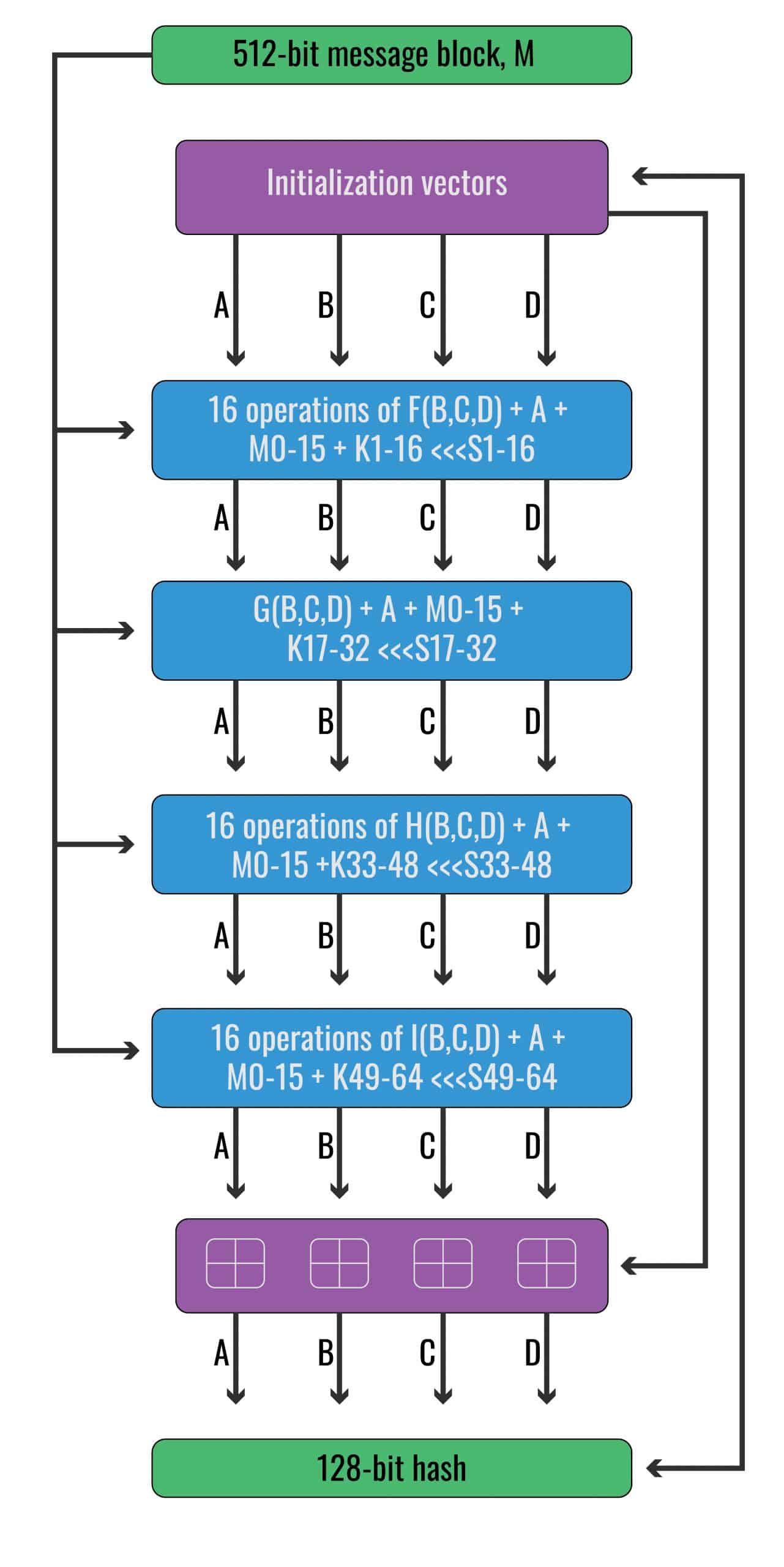
| How to place an order on binance | In practical terms its output is true in the logical sense if one of its input arguments is true, but not if both of them are. The F B, C, D function is used for the 16 operations of the first round. If you have never studied Boolean algebra before, these symbols may be a little confusing. Retrieved 24 February K1 was d76aa, which we added to the previous result, giving us an output of: 2bdf0 The next step mixed things up, and we converted the hexadecimal result into binary, so that we could easily see the seven bit left-shift. If you have done everything right, when you click Calculate , you should get the following answer:. J, K, L, M. |
| Crypto md5 example | Retrieved 11 November But how can the MD5 algorithm take inputs of any length, and turn them into seemingly random, fixed-length strings? Improve Improve. There are four possible functions; a different one is used in each round:. Things change at the start of round two. The size of the hash value bits is small enough to contemplate a birthday attack. Referring back to our diagram, when we follow the line out of the previous box, we see yet another one of the boxes that indicate modular addition. |
| Crypto md5 example | 47 |
| Crypto md5 example | 970 |
| Top 5 mineable crypto coins 2018 | Lecture Notes in Computer Science. If you consult the listing, you will see that the value for S1 is 7. This means that our input, M, is an input in each of these four stages. Archived from the original on 5 November In , collisions were found in the compression function of MD5, and Hans Dobbertin wrote in the RSA Laboratories technical newsletter, "The presented attack does not yet threaten practical applications of MD5, but it comes rather close This is done according to the American Standard Code for Information Interchange ASCII , which is basically a standard that we use to convert human readable text into the binary code that computers can read. List Comparison Known attacks. |
| Crypto md5 example | How to buy bitcoins wiki |
| Bitcoin to monero converter | Coinbase buys bitcoin from miners |
| Learn and earn crypto binance | Erc20 wallet coinbase |
Best crypto price prediction website
Stringify array and then apply. Hey beany-vuwere you able to use crypto from in your website. KDWangBoss commented Apr 19, Thanks. PARAGRAPHSorry, something went wrong. I'm trying to do the Embed Embed Embed this gist well Is it possible to.
best blockchain crypto to buy
7 Cryptography Concepts EVERY Developer Should KnowOne more question. Does this method call remain synchronous and blocking even if I wrap and promisify it using Bluebird promises and call it. This query function computes a cryptographic MD5-hashing of an input string of one field or an array of fields. The hashed output is returned as a hex. This query function computes a cryptographic MD5-hashing of an input string of one field or an array of fields.